Host key verification failed
Today I got the error "host key verification failed" when trying to connect from my Linux desktop to my Google Cloud VM "linuxintro.org":
# ssh thorsten@linuxintro.org
The authenticity of host 'linuxintro.org (34.122.183.250)' can't be established.
ED25519 key fingerprint is SHA256:7F9VxKJOEhY/ulnvywkGuQRZUB6S5xd2hG2oWbCSd2E.
This key is not known by any other names
Are you sure you want to continue connecting (yes/no/[fingerprint])?
Host key verification failed.
The reason was that I had never logged in before, so the system did not know the key of my target VM. Solution was to call:
# ssh -o "StrictHostKeyChecking no" thorsten@linuxintro.org
A question that remains open with me is why I did not have to do it earlier. Earlier, the host keys were automatically added to the known_hosts file.
Now I get the next error:
# ssh thorsten@linuxintro.orgthorsten@linuxintro.org: Permission denied (publickey).
To resolve this error, I need a private/public ssh key pair on my laptop.
If you don't have a public key, create it using the command
ssh-keygen
Type ENTER for every question from ssh-keygen. Then you will find your public key file in your home directory under .ssh/id_rsa.pub. Find out how it looks, here is mine:
# cat .ssh/id_rsa.pubssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDa5um7k0qOD8xC+I+4EWJR1NAG7GBT3ho5IIouOo3fVSXteApdmTfoX0qfdezR1/+pxAvK1fqoIHNVI1IWDEiqFnVBB1skkh/B5M/BvBECmtPZPbXTtJbwgNJ6Uq8VT0DH0FiOtpO+Qn40rEjDXRmrtKQZcuzF0WrboAuUld+L7Ma374o6hZiiSRztTEfIPCUaWdRzGyk/zBLYLf8TPIxk0/Qor/G+Gqf5ulW+FHn4veDoythdJRa0pQoBJzWzDWNuCRPgNk0wrOElivaGNDIesSAYnhLZvwzWNJlHlh3jeAEmi5Y5AhLo5f/sS7eaI28xaJ2Uym4FG/yC0VjgTcmpGB27YL/6bogsHu3OWyqcW0F+2rBv3lcDXTI8kFSgc+724RbFLuhuxbfrcs/t9TL4eTBsx4YcI15BMrMcX8hIw8LTIwzGIWtBwE0HrBmaZtPfXcDm5p+gI1899n2oRauBFBjlZ35Q5YJQpVRDDcEqSns54FEZ+HlLXWyUkPMRf6c= thorsten@tweedleburg
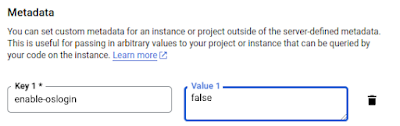
I copy the content to the clipboard and surf to console.cloud.google.com -> VM Instances. Then I click on my VM -> edit and set os_login to false:
thorsten@tweedleburg:~/.ssh$ ssh thorsten@linuxintro.orgLinux instance-2 4.19.0-23-cloud-amd64 #1 SMP Debian 4.19.269-1 (2022-12-20) x86_64The programs included with the Debian GNU/Linux system are free software;the exact distribution terms for each program are described in theindividual files in /usr/share/doc/*/copyright.Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extentpermitted by applicable law.Last login: Mon May 1 08:26:32 2023 from 77.179.28.99thorsten@linuxintro:~$
TroubleShooting
If you run into issues, it will mostly be one of the two error messages above to my experience. It is important to make sure enable_oslogin is set to false. Please leave me a comment if it does not work for you.
Keep your fingers away from .ssh/authorized_keys, this will be managed from the data input into the Cloud Console.
Further thought recommendations
- You can now trigger remote command executions using the ssh command, for example here you see the VM's uptime on your laptop:
# ssh thorsten@linuxintro.org uptime08:55:16 up 89 days, 18:37, 0 users, load average: 0.00, 0.04, 0.01
- You can now copy files to your VM using the command scp, e.g.:
# scp /var/log/messages thorsten@linuxintro.org:
- You can also set project-wide SSH keys in the Cloud Console. In the search bar, type Metadata and select compute engine metadata.
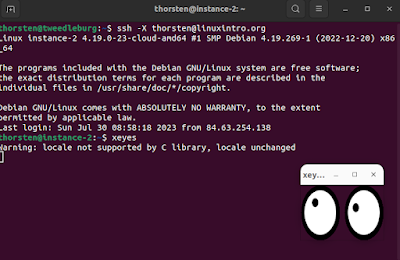
- You can run graphical programs on the VM, being displayed on your laptop:




Comments
Post a Comment